Arghh … finally there is some subdomain website where deface affected on domain telkomuniversity.ac.id. What the hell is that “deface”?
Deface is one of the actions to change the look of a good website home page or other pages that are linked in a url with the website.
The most easily beaten to change the contents of a web page is modification on index.php, because usually default to load a website is the file index.php. In addition to index.php, the hackers who deface on a website will store the backdoor, so “deface” could run again if the the index.php has fixed.
Why is the index.php can be changed? Is someone who wants to change the file content of a website must have access to the web, in the form of ftp access and a web admin? Well .. actually does so, but sometimes configuration and web hosting that one can cause a web have cracks resulting perforated hacker could enter and make changes on our website.
Causes of this broad gap include:
- Origin live server configuration, without any additional configuration of specific security and defense (security and firewall), and the configuration folder permissions are incorrect.
- Never update server
- Install cms with standard (not many special modifications)
- Do not add the plugin security and firewall correctly and appropriately
- Never update cms along with the plugin
- Access password option that is predictable
- Too many people that address admin yet uncontrolled
To prevent undesirable events, then you should do the opposite of that described above.
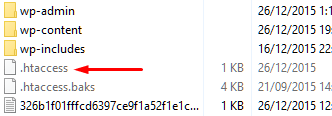
Especially for the first point, I will explain about the security in the form of adding additional .htacces file in the root folder of our website, particularly for WordPress CMS.
.htaccess it self stands for Hyper Text Access, is a file that typically referenced web access server to access files on a website.
Fill .htaccess for WordPress CMS defaults in the root folder is:
BEGIN WordPress
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteBase /
RewriteRule ^ index .php $ – [L]
RewriteCond% {REQUEST_FILENAME}! -f
RewriteCond% {REQUEST_FILENAME}! -d
RewriteRule. /index.php [L]
</ IfModule>
END WordPress
It’s been nice if it had a profit and .htacces with such content, if you want more steady, can be added to other fields, namely as follows:
- Stuffing .htaccess .htaccess file to protect itself from usahan to alter or remove the content, the content is;# STRONG PROTECTION .htaccess
<Files ~ “^. * . ([Hh] [Tt] [Aa])”>
order allow, deny
deny from all
satisfy all
</ Files> - Prevention not to allow reading folder website# disable directory browsing
Options All -Indexes - Wp-config.php protection of business reading, change, deletion. wp-config.php is a file that contains the database connection Air CMS WordPress website, and this is an important file that ensures the website of wordpress can live.# Protect wp-config.php
<files wp-config.php>
Order deny, allow
Deny from all
</ files> - Prevent script injection, by doing this, the WordPress blog you will be safe from businesses script injection and unwanted access and change efforts _REQUEST and / or globals.# Protect from sql injection
Options + FollowSymLinks
RewriteEngine On
RewriteCond% {QUERY_STRING} ( <|% 3C). * Script. * (> |% 3E) [NC, OR]
RewriteCond% {QUERY_STRING} globals (= | [| % [0-9A-Z] {0,2}) [OR]
RewriteCond% {QUERY_STRING} _REQUEST (= | [| % [0-9A-Z] {0,2})
RewriteRule ^ (. *) $ Index.php [F, L]
So overall content of more advanced .htaccess for WordPress CMS in the folder admin / root is:
# BEGIN WordPress
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteBase /
RewriteRule ^ index .php $ – [L]
RewriteCond% {REQUEST_FILENAME}! -f
RewriteCond% {REQUEST_FILENAME}! -d
RewriteRule. /index.php [L]
</ IfModule>
# STRONG PROTECTION .htaccess
</ code>
<Files ~ “^. * . ([Hh] [Tt] [Aa])”>
order allow, deny
deny from all
satisfy all
</ Files>
# Disable directory browsing
Options All -Indexes
# Protect wp-config.php
<files wp-config.php>
Order deny, allow
Deny from all
</ files>
# Protect from sql injection
Options + FollowSymLinks
RewriteEngine On
RewriteCond% {QUERY_STRING} ( <|% 3C). * Script. * (> |% 3E) [NC, OR]
RewriteCond% {QUERY_STRING} globals (= | [| % [0-9A-Z] {0,2}) [OR]
RewriteCond% {QUERY_STRING} _REQUEST (= | [| % [0-9A-Z] {0,2})
RewriteRule ^ (. *) $ Index.php [F, L]
# END WordPress
In addition, it is worth adding .htacces in wp-content folder, the contents of the folder as it relates to themes, plugins, and estate website content, its contents should be as follows:
Order deny, allow
Deny from all
<Files ~ “. (Xml | css | jpeg | png | gif | js) $”>
Allow from all
</ Files>
Add another file that was calculated to be critical, for example, the extension office and zip files, never add extensions to the executable files.